8 01 2016
Openshift 3 – Create my custom router/haproxy
Router in openshift is a simple docker haproxy image and can be customised. In order to learn how customise the router, we will add an ACL into haproxy config. The goal is to restrict the traffic through the router by allowing only a specific source ip.
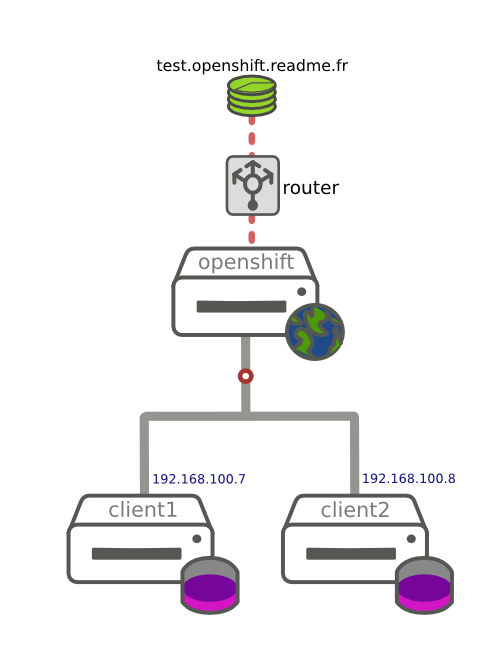
test.openshift.readme.fr is a simple app created in openshift3. Client1 and client2 can access to the app via the router.
Customise the router image
Firt step is to get the haproxy configuration template (haproxy-config.template) from the openshift router upstream image (ose-haproxy-router). And then perform your changes.
Edit the template and add ACL to allow only taffic from 192.168.100.7 (client1)
Lets do a new openshift router image from the upstream one and copy our new template inside.
To be able to push our custom image directly into the ose registry, we need to commit our image and apply a tag with the ose registry service ip (if you are not in the same network, you should use docker save and docker import)
Get the ose registry service ip
Commit the new image and tag with the ose registry service ip
Push the router image
Next step is push the new image into the ose registry. You need an account with enough right to push into our wanted namespace. In our case we will push into the openshift namspace with a specific admin user (rcip-admin)
rcip-admin is our internal admin account, this is how we set the role admin on the openshift namespace to be able to push into it.
Now get the token to be able to log into the internal ose registry
Log into openshift OSE registry
Push the custom commited image
The custom router is uploaded, we can try to create the router in openshift
Testing time
Ok, test to access on an already deployed app test.openshift.readme.fr route. We expect client1 works and client2 sould be refused.
We are able to get our application from client1
Client2 is correctly rejected by the custom router
Decode EXIF from a raw photo Openshift registry on Amazon S3